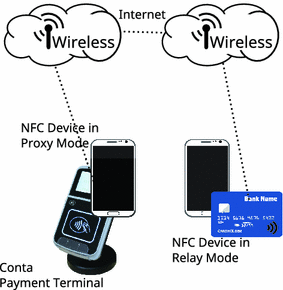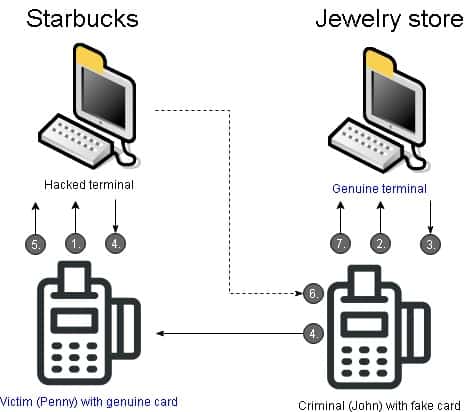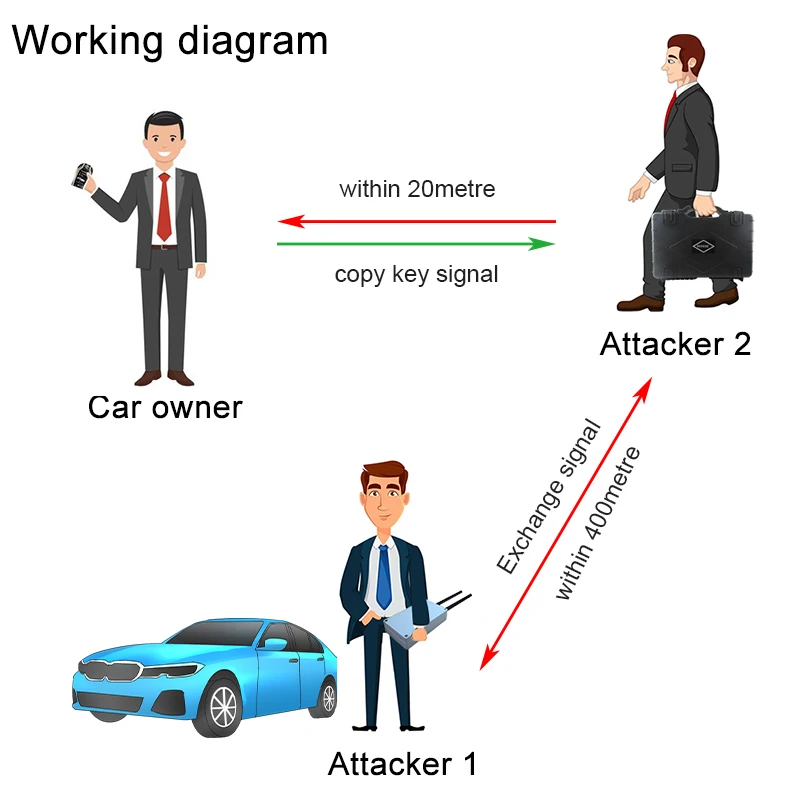
Car Unlock Device Car Relay Attack Devices Anti Theft Car - Buy Anti Cheft Car,Car Unlock Device,Car Relay Attack Devices Product on Alibaba.com

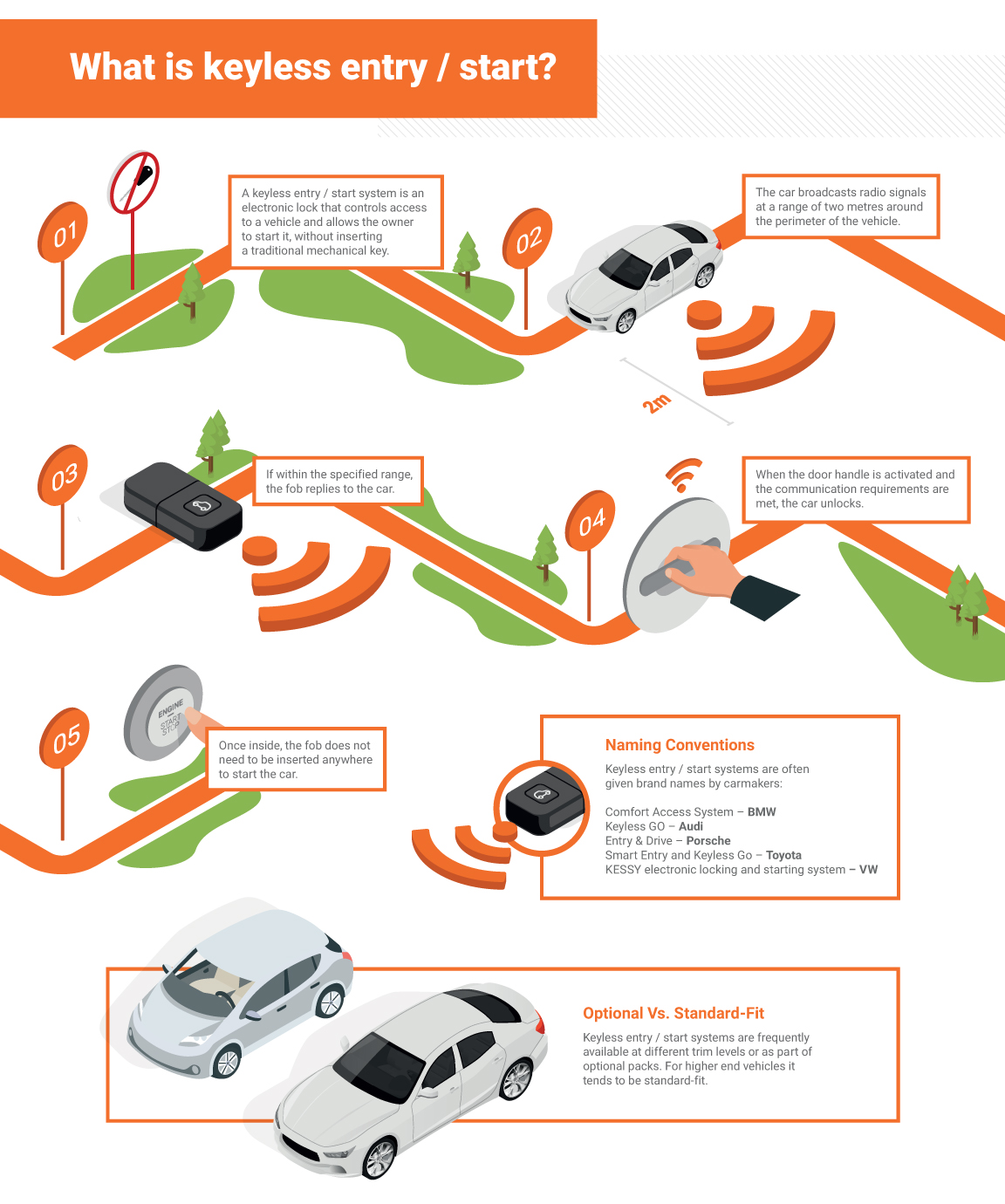
Keyless car theft: What is a relay attack, how can you prevent it, and will your car insurance cover it? | Leasing.com

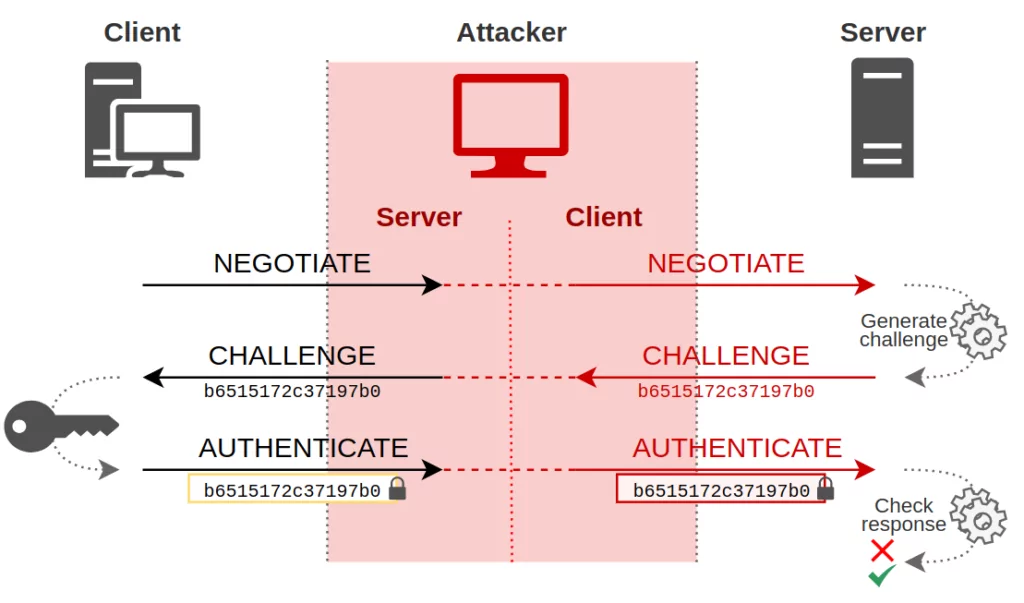
The relay attack in practice: (a) opening the door with the relay. (b)... | Download Scientific Diagram
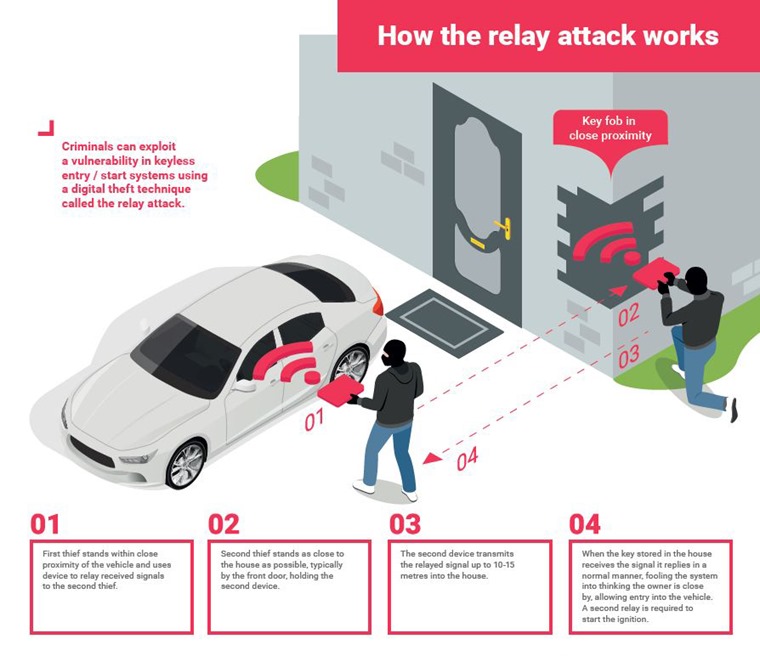
Keyless car theft: What is a relay attack, how can you prevent it, and will your car insurance cover it? | Leasing.com

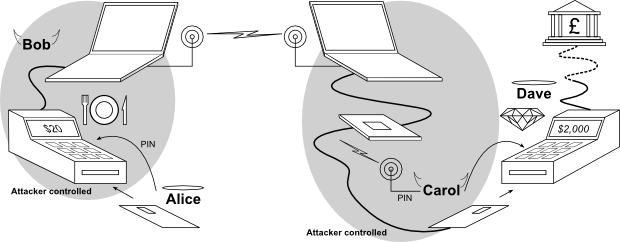





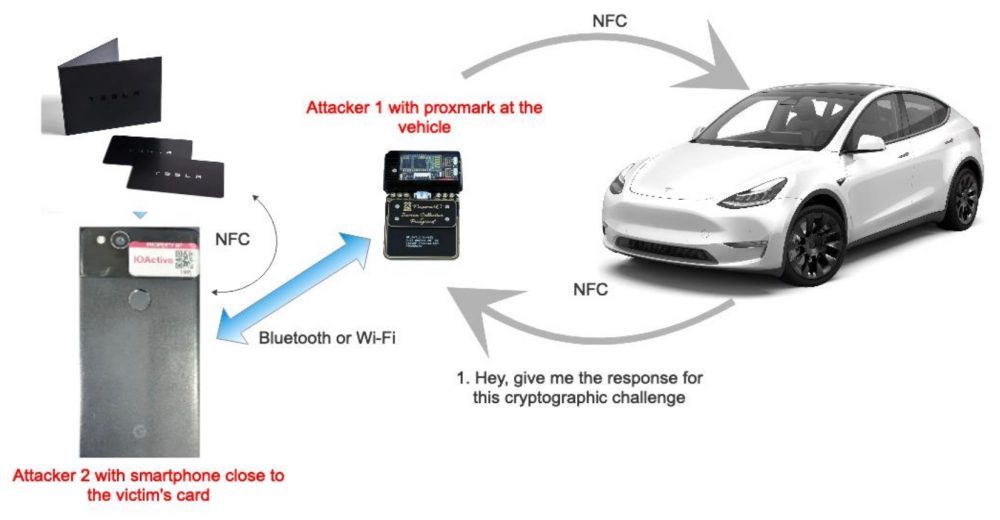
![Video] Hackers Steal Tesla Model S using a Relay Attack Video] Hackers Steal Tesla Model S using a Relay Attack](https://blog.drhack.net/wp-content/uploads/2018/10/Passive-Entry-Relay-Attack-Tesla.jpg)