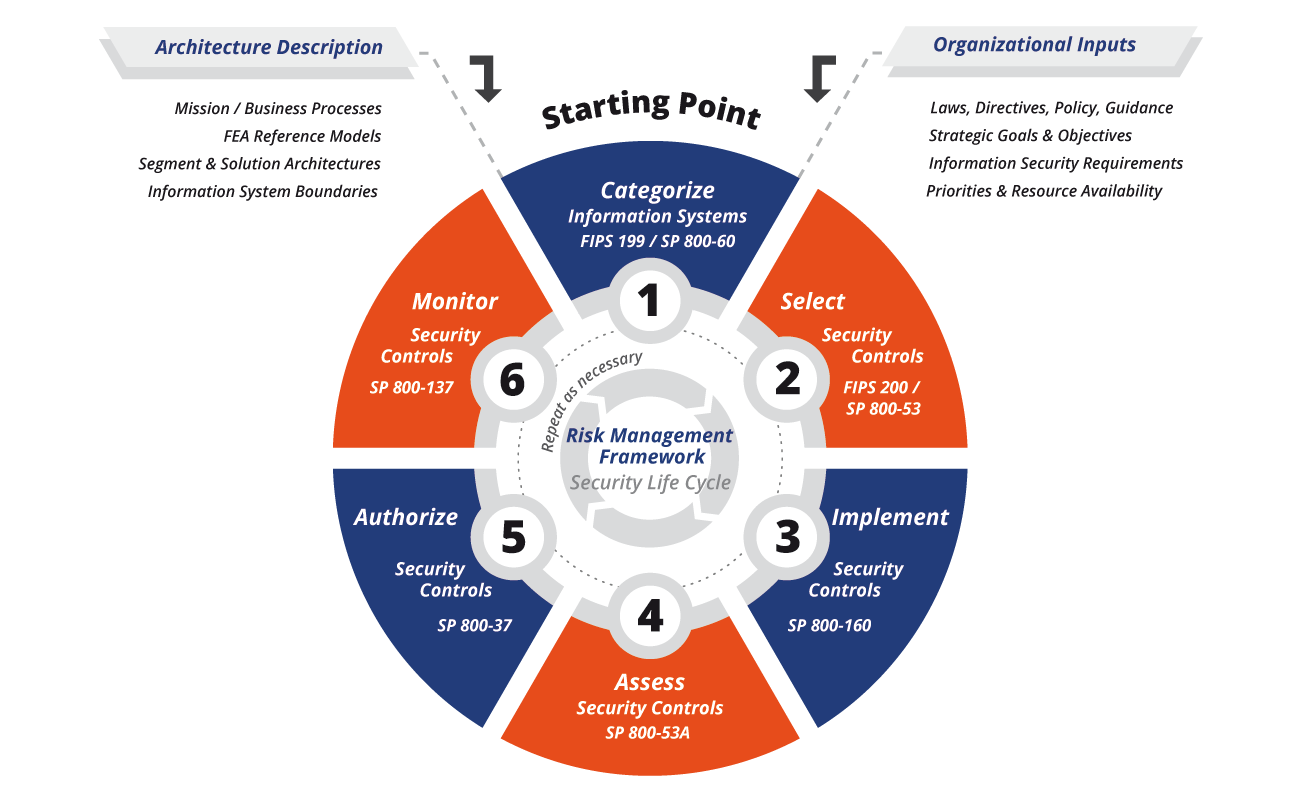
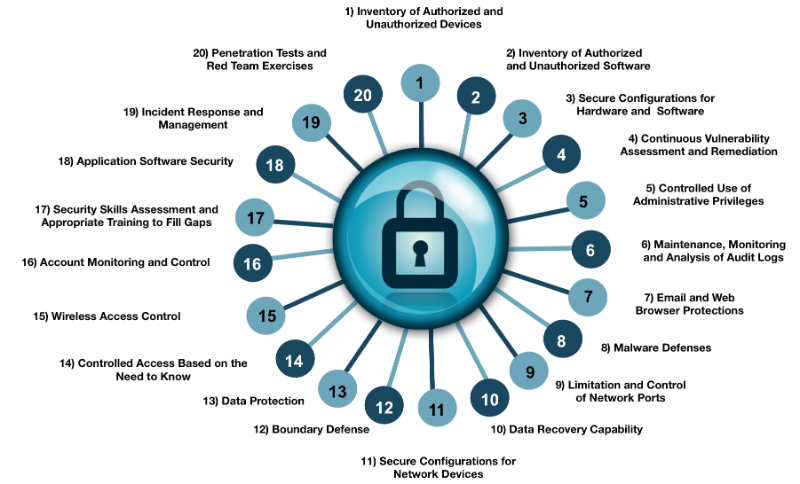
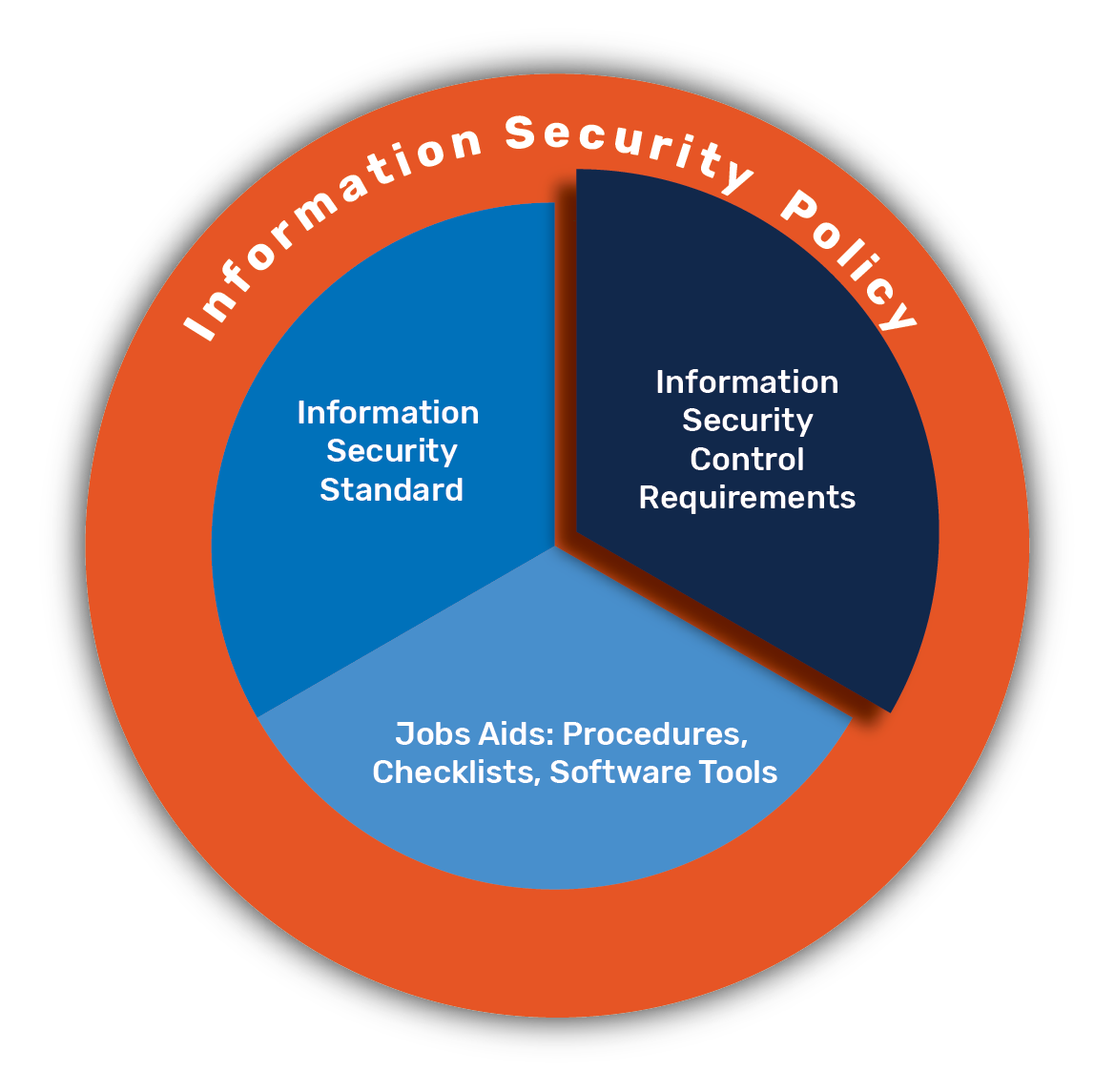
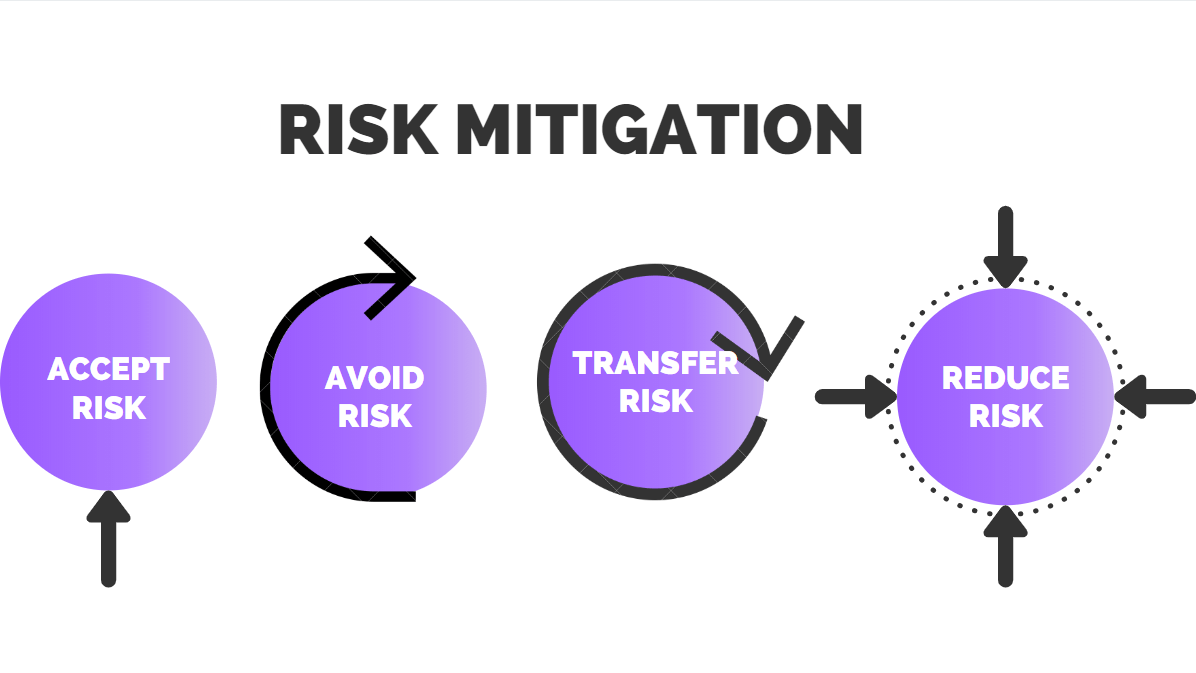
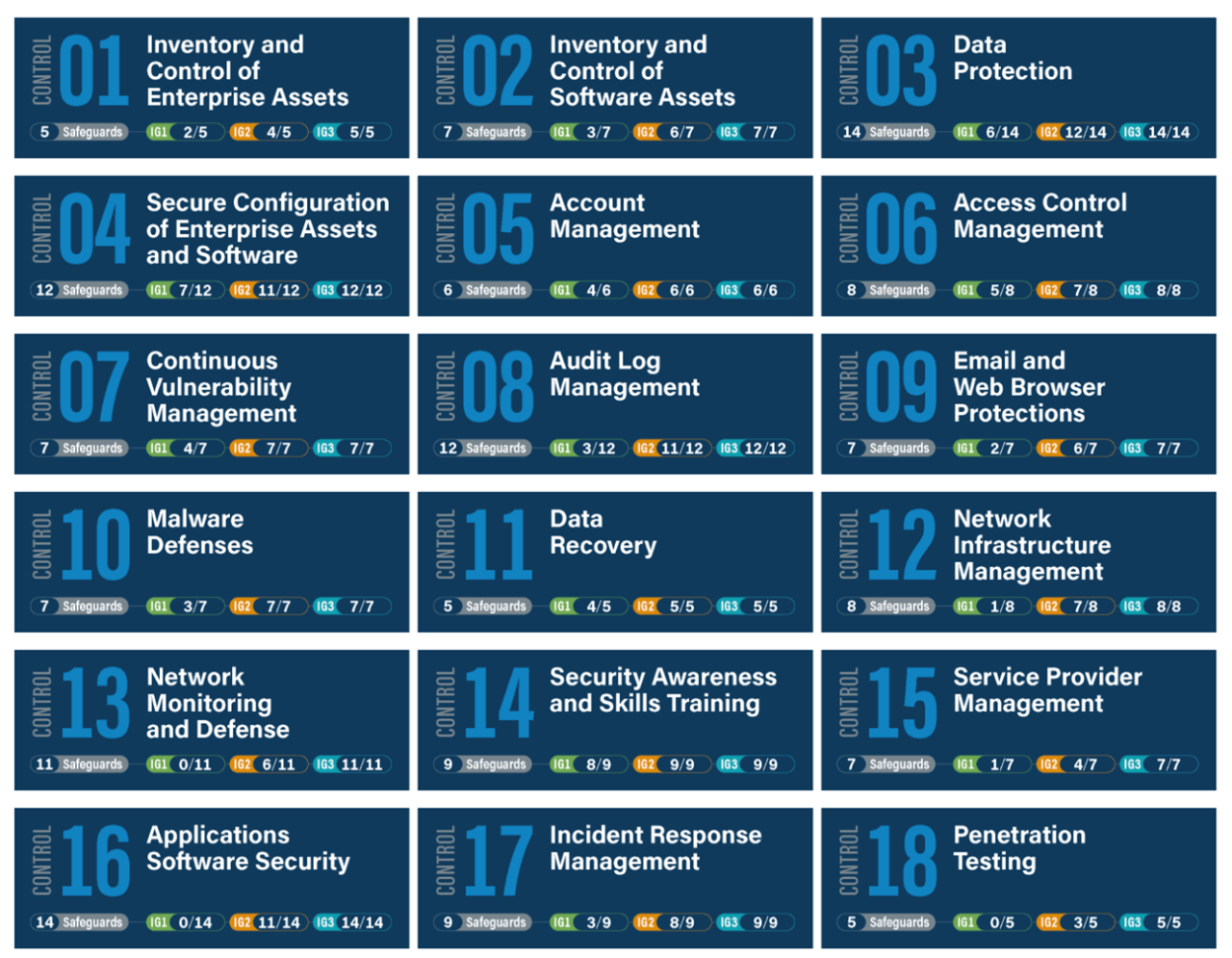
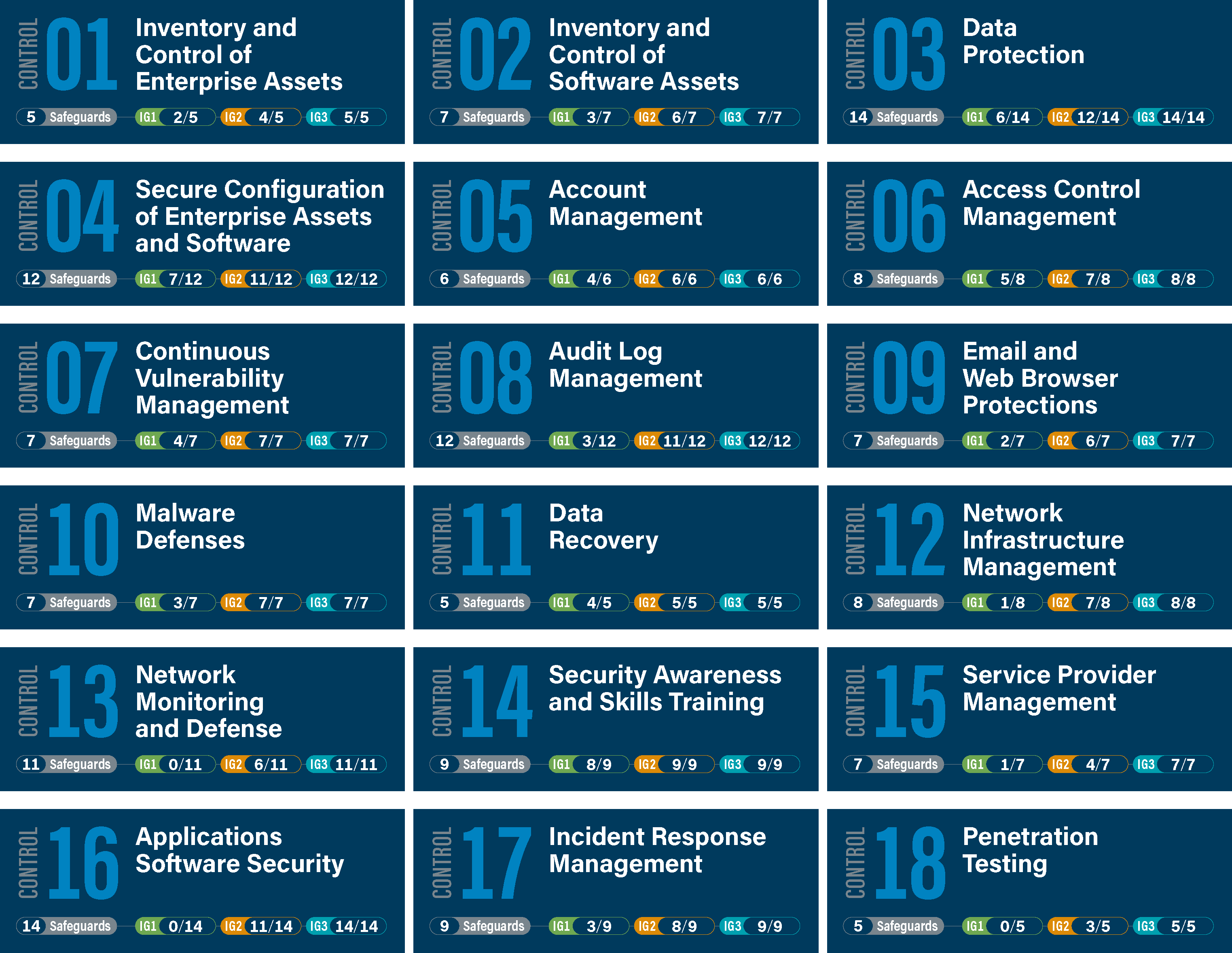
Tabular Presentation Of Security Controls Categorization | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
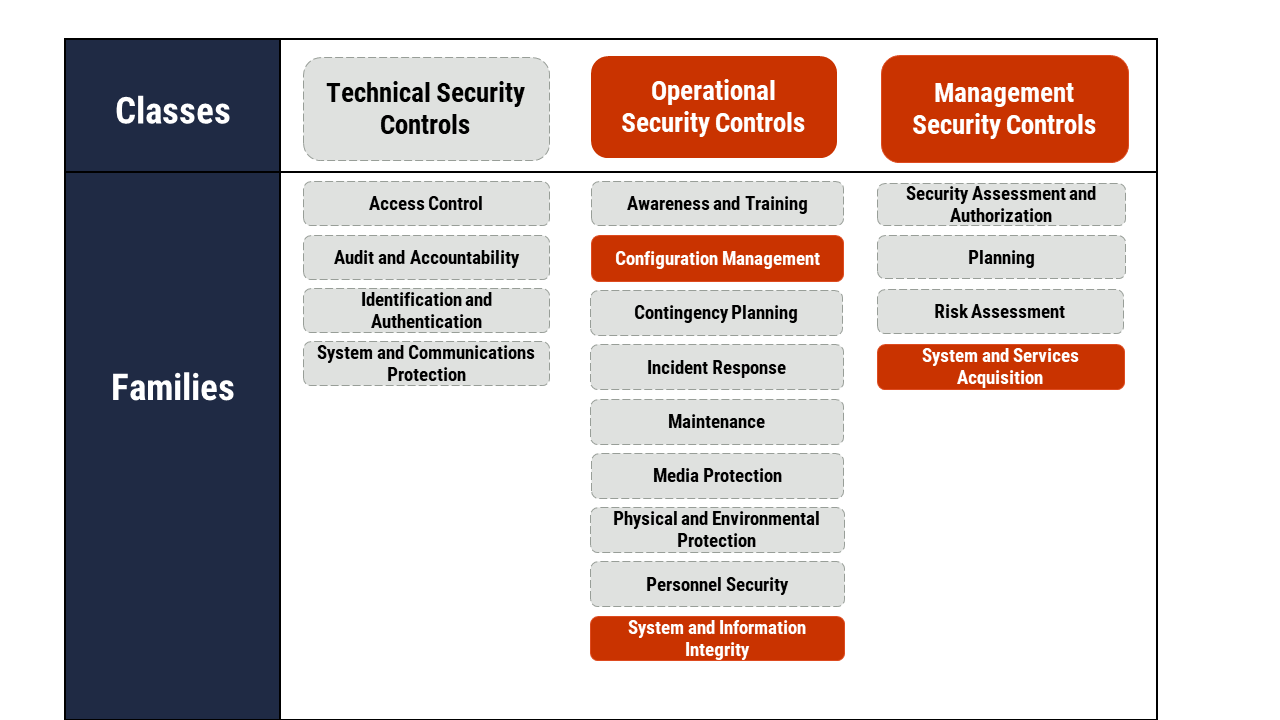
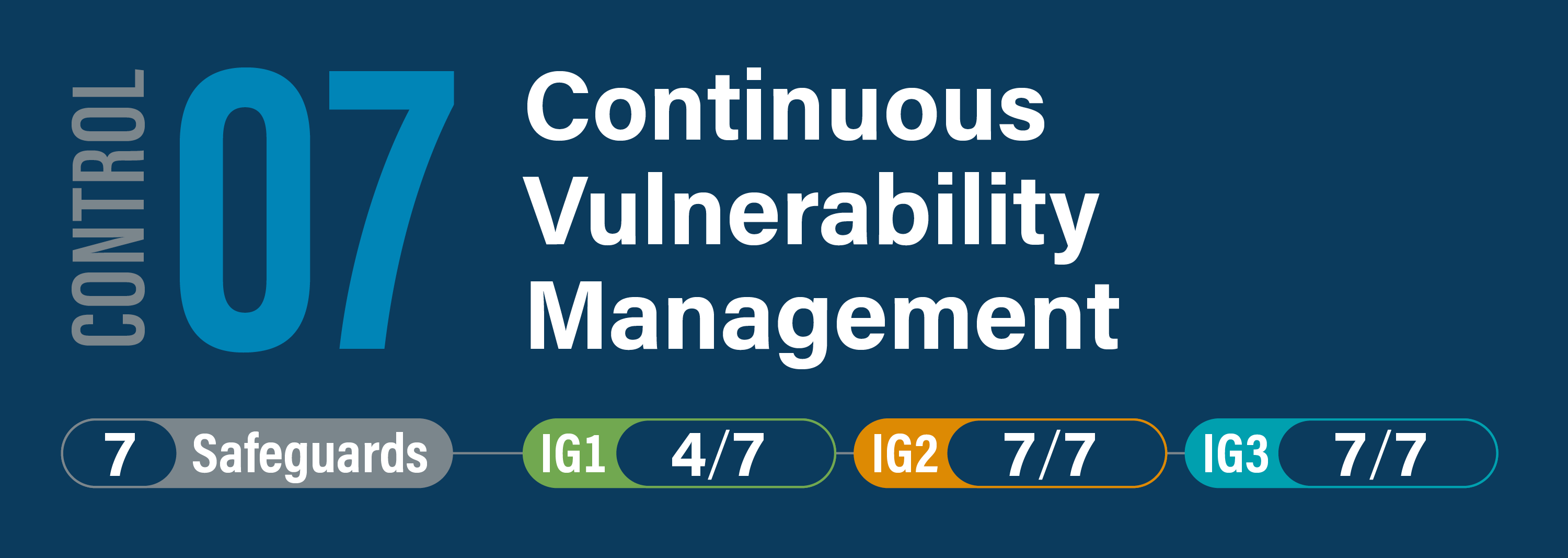
Top 10 IT security action items: No.2 patch operating systems and applications - ITSM.10.096 - Canadian Centre for Cyber Security